
Malicious npm Packages Used in Targeted Phishing Attack: What Security Teams Should Know
Over 1.3 million packages are available on npm. 95% of modern web applications rely on open-source components like those found on npm. A single compromised npm package like event-stream affected millions of users before it was caught. It was live for months before detection.
Recently, a targeted phishing campaign tricked developers into logging into a fake npm site, npnjs[.]com, stealing credentials and pushing malicious versions of popular packages like eslint-config-prettier and eslint-plugin-prettier. These updates bypassed normal GitHub review processes, leading to silent remote code execution (RCE) on Windows endpoints.
Timeline of Events
- Mid-July 2025: Attackers deployed phishing infrastructure (npnjs[.]com) mimicking the official npm site.
- Credential Theft: A maintainer’s npm token was compromised.
- Malicious Publish: Attacker pushed tainted versions of widely used packages without any corresponding GitHub commits or PRs.
Malicious Packages Identified
- eslint-config-prettier: 8.10.1, 9.1.1, 10.1.6, 10.1.7
- eslint-plugin-prettier: 4.2.2, 4.2.3
- synckit: 0.11.9
- @pkgr/core: 0.2.8
- napi-postinstall: 0.3.1
What does this attack look like on an endpoint?
The victim user downloaded a malicious eslint-config-prettier package through npm. This package dropped a DLL (node-gyp.dll) via a hidden postinstall script. Once triggered by rundll32.exe, it connected to suspicious domains like firebase[.]su, granting attackers covert remote access.
Observed Activity (Process Tree)
bash.exe
→ sh.exe
→ node.exe
→ cmd.exe
→ node.exe install.js
→ rundll32.exe node-gyp.dll
How can Culminate AI SOC Analyst help?
A medium severity EDR alert is triggered because of the Defense Evasion attack where rundll32.exe executed low-reputation arbitrary code from node-gyp.dll, connecting to suspicious URL firebase[.]su and IP address 104[.]21[.]32[.]127. Culminate performs deeper investigation as follows:
- Traced the full process chain including script and DLL execution.
- Flagged abnormal DLL behavior and outbound connections to suspicious, newly registered domains.
- Surface the dropped files, enabling quick identification of payloads like
node-gyp.dll.
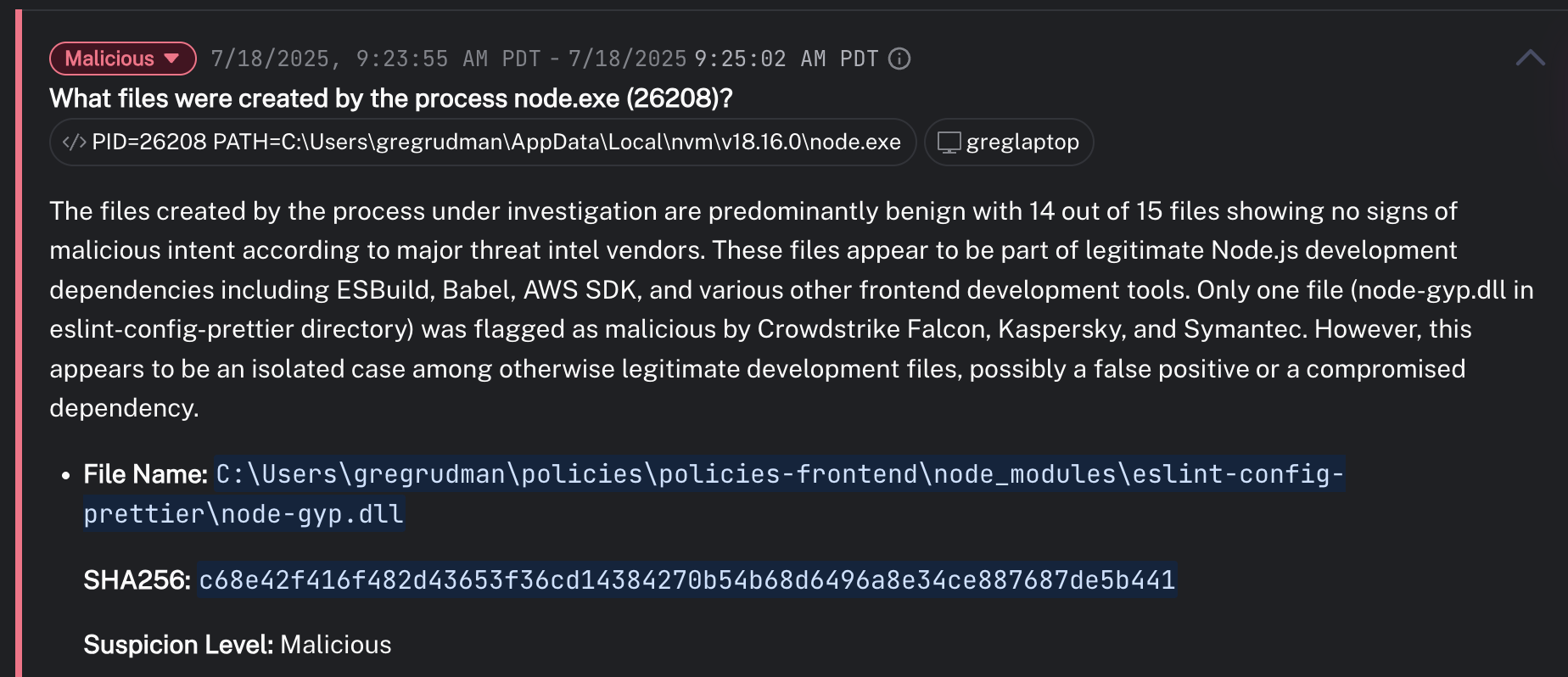
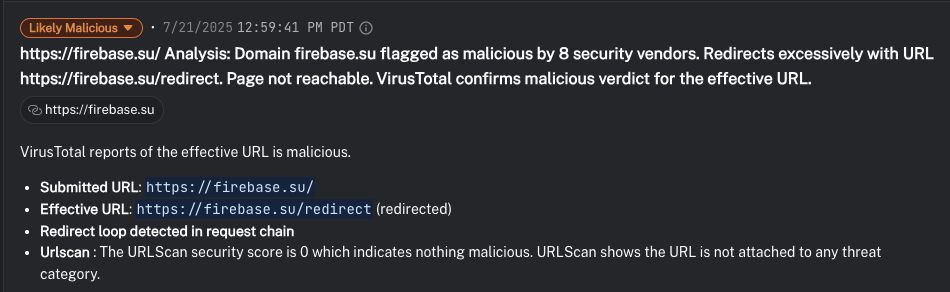
Culminate uses real-time domain age checks. The system raised an alert when a process connected to firebase[.]su, a domain less than a year old — a suspicious indicator of C2 or exfiltration activity.
Culminate’s AI SOC Analyst is built to catch advanced threats including supply chain attacks. Culminate AI SOC Analyst discovers full incidents from even medium and low severity alerts which SOC teams typically do not have bandwidth to review. Our AI SOC Analyst uses the techniques described below to detect threats beyond execution.
- Flags suspicious behaviors such as:
- DLL execution (e.g., node-gyp.dll via rundll32.exe)
- Unusual or suspicious process chains
- Outbound traffic to domains like firebase[.]su
- Correlates telemetry across:
- Endpoints
- User behavior
- Logs from all security tools like Office 365 and Defender
- Rapidly investigates and escalates real threats
- Helps security teams contain the attack before it spreads






